HTTPS is a way to securely transmit data over the internet, which is essential for business owners and consumers. Website owner enables HTTPS port TCP 443 to secure web pages, online transactions, email communication, and other types of data transfers on the internet.
While running a site, we usually see ‘HTTPS’ or ‘HTTP’ at the start of the web address. The HTTPS site seems secure because the padlock icon at the address bar indicates the secure communication channel. Still, when we try to access a labelled HTTP site, the browsers display a security warning stating “Not Secure”. This indicates that communication over this site is dangerous, and that’s where we need HTTPS.
Encryption configuration checks are one of the important pillars in our pen testing and web application and API pen test methodologies. It ensures that website security checks provide that data encryption in transit is in line with best security practices.
HTTPS stands for HyperText Transfer Protocol Secure, which protects web browser communication. It secures the connection by encrypting the traffic transmitted over HTTPS port 443, protecting customer data in transit.
As an increasing number of people use mobile devices with browsers that do not support HTTPS port 443 connections by default, we need to be more aware than ever about protecting our information when browsing online. This blog post will give you all the basics you’ll need to know about HTTPS port 443.
What is the HTTPS port?
Before going into the details of HTTPS port, it is required to understand what port means and how it works. To define it simply, a port is an entry and exit point. A network port establishes an endpoint communication between two computers or mobile devices in computer networking. When the website sends a service request to the web server, it uses a network port dedicated to the requested service. The server connects to the port and sends back the service, which the website will receive on the same port.
The transport layer of the TCP/IP (Transmission Control Protocol/Internet Protocol) model sets these ports, distinguished by the numbers with different network operations. These network ports are virtual and used for different services; for example, port 21 is used for FTP (File Transfer Protocol), port 53 is used for DNS (Domain Name System) etc. Their numbers identify the ports to guide different types of web traffic on a site.
What port does HTTPS use?
443
IETF (Internet Engineering Task Force) has standardised protocols for specific ports. Technically, you can use port 443 for HTTP traffic or 80 for HTTPS or any other port.
What is port 443?
HTTPS port 443 is used to secure a communication channel between two devices, usually termed in the language of computer networking as a client, i.e. a web browser and a server, i.e. web server. It creates a secure channel by encrypting the traffic with security certificates, i.e. SSL certificates.
As mentioned, all network ports are distinguished by port numbers for specific services. Port 443 is globally used for HTTPS service that provides data authentication and encryption. The HTTPS traffic gets encrypted by using cryptographic algorithms called SSL/TLS. SSL (Secure Sockets Layer) uses an asymmetric encryption algorithm. At the same time, TLS (Transport Layer Security) is the more secure version of SSL that has addressed the security flaws of the previous version. Both protocols provide SSL certificates to enable the secure transfer of encrypted data over port 443.
Why do we use port 443?
A website and a server connection are made via port 80 or 443. Port 80 is used for HTTP service, which does not provide any security for the data to be travelled, while port 443 is used for HTTPS service, that’s the primary purpose of securing the communication channel. If we talk about today’s era, where the rate of cybercrimes is increasing rapidly, not blocking the traffic could lead to the potential loss of sensitive data, i.e. passwords, credit card information, customer personal information, business-critical data etc. For that purpose, it is essential to use a secure channel where data is encrypted, and even if an attacker attempts to steal that data, he cannot compromise it.
Because of the growing customer demand, website owners secure their sites with HTTPS port 443. People now prefer to transact on a site that supports HTTPS connections as it is safer. In contrast to HTTP, the data travels in plain text, which is likely vulnerable to compromise.
The below chart shows the approximate transmission of encrypted traffic over port 443 across Google as of 01 January 2021.

Is HTTPS always port 443?
Port 443 is primarily used for handling HTTPS traffic, but it is important to note that HTTPS traffic can also be transmitted over port 80. Using this port for HTTPS does not mean that your connection is secure. As mentioned, these ports are just entry and exit points distinguished by globally assigned numbers for accessible communication.
HTTPS Port 443
Port 443 guarantees that the site runs on an HTTPS version, but if port 443 is unavailable, the site will load on the insecure connection over port 80 if allowed by the website configuration.
Similarly, if you want to use any port other than 443 for HTTPS, a web owner must change the settings manually and make appropriate changes to avoid misconfiguration.
How to open ports in the firewall?
Stephen Hawking famously wrote, ‘half the battle is showing up’. Before you learn and make changes to your firewall configuration, it’s essential to ensure there is justification to open a port in the firewall, or is it just YOU? First, check if a port is open on a firewall and allows access to port 443. Most firewalls allow outbound access by default to web ports such as 80 and 443.
On a computer that is behind the firewall (behind the firewall means located inside the protected perimeter of a firewall/device), try this:
If you can see the content displayed on the BBC homepage, you can access port 443. Pay attention to the lock on the leftmost position in the URL bar:
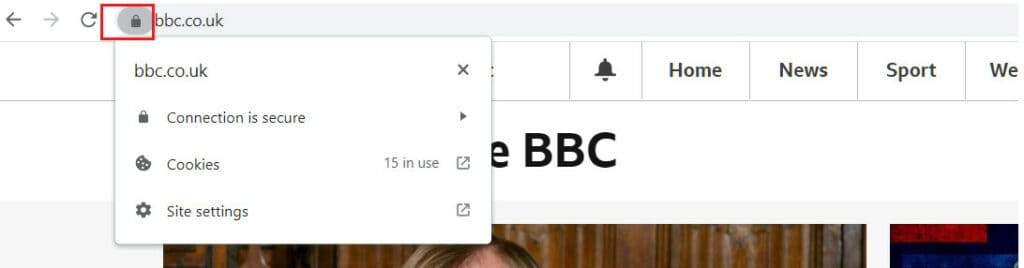
If you do not see any content displayed, errors or error pages, study the error type shown on the page. For this discussion, we will show how to open a firewall port on various platforms below.
How to open port 443 in Windows 10?
- Select Start – Run and enter firewall. cpl. This should take you to the firewall control panel. Alternatively, to browse with the mouse, go to the Start menu – Control Panel\System and Security\Windows Defender Firewall.
- Select Advanced Settings in the left column and click Inbound Rules.
- Right-click Inbound rules – New rule.
- Select Port and Next, then TCP, enter the port number (one or many – comma separated) in the specific local ports field, such as 443,444,445, and click next.
- Select Allow the connection and click Next.
- Select Domain and Private, click Next and Name name wall rule’ Port 443 rule’, and click Finish.
- Click outbound rules.
- Rinse and repeat based on how many ports/services/programs you must set to allow through your firewall.

Now, select the ‘custom’ rule type if you know all about different ports, services, and programs to define a custom rule; otherwise, select the ‘port’ option to specify a port-based rule in the firewall.

How to open port 443 in Linux?
Use ‘iptables‘ to allow web traffic on port 80, 443 or other ports of your choice you want to allow. iptables is the default choice on many Linux flavours.
Run the following command to open port 443
iptables -A INPUT -p tcp -m tcp --dport 443 -j ACCEPT
To save the iptables rules after config change
sudo service iptables save
To restart the iptables after changes
service iptables restart
How to open the port on the router?
See below for how to open the configuration page. If you know this step, go to step 2, ‘Find settings…’.
- Open the router interface/admin page by typing HTTPS:/// into your browser. The easiest way (most likely) to find your router address at your home is to go to the start menu and type run – Best match shows the ‘run’ app – click enter.
- This opens a small prompt on the bottom left-hand side; type cmd next to the Open field and press Enter.
- Now type ipconfig and find the relevant Adapter (If you are on wired, it should say Ethernet adapter Ethernet or on Wi-Fi, you will see Wireless LAN adapter Wi-Fi or similar).
- Find the IP address against ‘Default Gateway’. In some cases, it could be 192.168.1.1 or something different.
- Now type that IP address with the prefix https://192.168.1.1/ in your browser. This should open your router’s admin dashboard or configuration page.
- Navigate to the dashboard or configuration page of your router.
- Find settings related to Ports, Forwarding, Port forwarding, Applications, Firewall, Protected set up or similar variations. Based on different vendors and their settings, this could be named differently.
- Open the port you want to add to the firewall config by adding the Application name, Port type (TCP/UDP or both), Inbound/Allow a connection and finish saving the settings.
Are there any standard alternative HTTPS ports?
Yes, 8443 is sometimes known as https-alt (alternative HTTPS port). Port 8443 is likely to have gained popularity from mod_nss, derived from the mod_ssl module of the Apache web server using Network Security Services (NSS) libraries.
Other famous uses of port 8443 are:
- The default port for Tomcat to run on HTTPS, an open-source Java servlet container that implements Java-Server Pages, java servlet, Websites API, etc.
- PC sync software uses port 8443 to transfer files
Is Port 8443 and 443 the same?
Both are ports that are used to serve web services. However, you do not need to add 443 in the URL when you add a prefix of HTTPS. For example, you can access a service on 443 by typing just https://abc.com/ (no need to add “:443” at the end as a port number). While browsing a web service on 8443, you must write the full URL, such as https://abc.com:8443/, to access a service on 8443.
What is HTTPS protocol, and how it works?
The HyperText Transfer Protocol Secure is an HTTP extension that manages secure and reliable communication over the Internet. The ‘S’ stands for the secure exchange of information between a client and the server. HTTPS is governed by the SSL/TLS responsible for encrypting the data throughout the entire communication and enabling the site to be more robust.
SSL/TLS protocol
When a web page sends information to the server., it gets encrypted using SSL/TLS. It uses the asymmetric encryption algorithm, which uses two encrypted and decrypt keys known as public and private. As the name suggests, the public key is distributed over the public network and available to everyone, while the private key is confidential and never disclosed to anyone. The public key encrypts the traffic only decrypted by its private key. Both keys are generated together and are distinct from each other but mathematically related. No one can ever generate the private key from its public key and vice versa.
SSL/TLS establishes secure communication on a website by using SSL certificates. SSL certificate serves the purpose of authentication, which enables the encrypted connection. The whole process is called SSL/TLS handshake. An SSL certificate for multiple domains will allow you to secure domain names, including the main domain names and up to 99 SANs (subject alternative names).
How does HTTPS work step by step?
An SSL/TLS handshake process establishes a secure connection between a client (a browser) and the server. Here is a step-by-step SSL/TLS handshake process of how a website and a server use SSL certificates to negotiate the secure exchange of information.
- Client Hello: At first, the client browser sends a message “Hello” listing the information relating to the connection, i.e. SSL/TLS version, the encryption algorithm and the data compression methods supported by the server.
- Server Hello: After receiving the message, the server responds by sending a message “Hello” containing the encryption algorithm agreement, session ID, server’s digital certificate (or the SSL certificate) and the server’s public key.
- Authentication: The browser would check with the certificate authority (CA) to confirm the certificate’s authenticity issued to the webserver.
- Client Key Exchange: The client sends a premaster secret – a random string of bytes. The premaster secret is encrypted with the public key token from the server’s SSL certificate and can only be decrypted by the server’s private key. Now, the server decrypts the premaster secret sent by the client. Now, the client and the server both generate session keys.
- Finished(client): The client, i.e. the browser, sends a “finished” message encrypted by its private key indicating the browser’s part from the handshake process is completed.
- Finished(server): The server sends the ‘finished’ message encrypted with a session key and responds to the browser, indicating the completion of the handshake process from its side.
- Secure symmetric encryption achieved: A fast symmetric encryption setup has been fulfilled once the handshake completes on both sides. The browser and the server now exchange information securely encrypted by their private keys.
After establishing the connection, the URL bar displays a padlock sign or an unbroken key in the status region – indicating the status of the secure connection.

TLS handshakes use asymmetric encryption (public and private keys). All handshakes do not use the private key during the session key generation process, e.g. DH (Diffie-Hellman) handshake.
Keyless SSL is another critical term to be aware of. Keyless, as the name says, is keyless, i.e. without private keys. Cloud vendors usually offer keyless SSL, where service providers leverage the TLS usage without asking for private keys from the customer. This way is considered more reliable because customers do not feel safe sharing their private keys for multiple reasons. Therefore, a private key is still used without sharing outside the customer company.
During implementation, a server with the private key stays within customer control (cloud or on-premises). The cloud vendor’s server forwards the necessary data for the handshake process.
What is a certificate authority?
Certificate Authorities are trusted entities that verify SSL certificates. They ensure the website’s identity by providing an SSL certificate as a credential to authenticate the site.
Certificate authorities issue several digital certificates to guide people for trusted transactions on a website and play a vital role in a secure browsing experience.

What are HTTP and its purpose?
HyperText Transfer Protocol (HTTP Protocol) is a prior version of HTTPS that serves as the foundation of WWW (World Wide Web) communication. The client-server protocol’s primary purpose is to govern how the traffic is modified and transmitted over the internet. It also defines what actions a client and the server should take while exchanging information.
When we enter a URL in the address bar, a command is sent to the server directing it to fetch the requested web pages.
Some important features of HTTP
- HTTP is connectionless – Once a connection is established between the client and server, the server responds to the client for a requested service and the connection is destroyed. If the same client wants to ask the same server, it will make a new connection again for each new request.
- Media is independent – The client and server can exchange any data. Before transmitting any data, the client and server must specify the data type based on the relevant MIME standard.
HTTP Request
A request is generated from the client to the server to establish a connection. The client website sends a request that contains a series of encoded data elements, including:
- URL indicates the requested resource on the web.
- HTTP version type shows the version.
- HTTP method indicates the requested action to be performed by the server.
- Request headers indicate browser type, data type and cookies.
- The optional body indicates the option information the server needs, i.e. user credentials or short-form responses submitted to the websites.

HTTP Methods
There are different methods used to request a specific task. Some of them are:
- GET requests information from the web server.
- POST submits information to the web server.
- DELETE removes the specified web resource.
- TRACE shows any changes made to the web resource.
- OPTIONS shows what methods are available for a web resource.
- PATCH modifies a web resource.
HTTP Responses
While responding to the request, the server sends a request status by issuing response codes:
- 200 OK indicates the request is processed.
- 300 Moved Permanently means the requested URL has changed permanently.
- 401 Unauthorised indicates the client or server is not authenticated.
- 403 Forbidden suggests the client does not authorise access.
- 404 Not Found means the requested resource does not exist.
- 500 Internal Server means the server has issues and cannot process a request.
Are HTTP and HTTPS protocols secure?
To answer this question, you can observe the definition of both. A site uses HTTP to pass and fetch information in plaintext, while HTTPS makes a more secure and reliable connection by enabling encryption for the transportation channel.
HTTP port 80
An HTTP site is safe if you do not enter sensitive information while browsing. Web developers designed HTTPS sites for online transitions, email communication or banking applications because it is safer.
Is HTTPS protocol secure?
The secure connection of HTTPS is based on the SSL or TLS version in use.
- SSL 1.0 was the first cryptographic algorithm but was never released publicly because of its flaws and vulnerabilities.
- SSL 2.0 was the first released in public but got replaced by SSL 3.0 for poor security.
- Next, SSL3.0 was also found to have some security deficiencies, creating the modified algorithm known as TLS.
- After the release of TLS, both SSL 2.0 and 3.0 were deprecated. The TLS 1.0 and its later version 1.1 were deprecated by Google, Microsoft, Apple and Mozilla due to their identified vulnerabilities.
- The commonly used secure versions for HTTPS connection are TLS 1.2 and 1.3, which are reliable and ensure a protected link.
The following table will summarise the website support of SSL/TLS versions as of April 2021 gathered by Wikipedia:
Please provide a valid CSV file.
The lower percentage of TLS 1.3 is due to the web browsers’ limited support fof this version. The above stats conclude that many users stick to the old SSL versions for which they are vulnerable to insecure HTTPS connections.
How to use 443?
On a Windows system, you can enable port 443 through the control panel – systems and security – firewall. Add a new inbound rule for rule type: TCP, specified local ports: 443 and action: allow the connection. It will ensure TCP 443 traffic is allowed into your system through the Windows host firewall.
To ensure you encrypt all communications, you can use the browser extension HTTPS everywhere by EFF (Electronic Frontier Foundation), available on all popular browsers.
Can I use port 443 for HTTP?
You can run HTTP on any port. However, port 443 is strictly for HTTPS and using well-defined ports would mean users do not have to specify the port number. For example, a user visiting https://thecyphere.com/ will see their browser making an HTTPS request.
Web servers use port 80 to listen for requests from the public internet. Port 89 can be used as a substitute if you want people to access your site over insecure connections (the same way they would with port 80).
Conclusion
Intruding unencrypted data over a vulnerable channel is one of the common examples of cyber attacks. The data travelling in plain text without encryption can be easily compromised if it gets into the wrong hands. That data could be the user’s personal information, including credit card data, usernames and passwords, IP address, business data and many more. To avoid this risky approach, users prefer a safe internet connection to communicate where the data is less likely to be compromised.
HTTPS provides a secure channel between the client and the server to serve this purpose. It uses a network port 443 to transmit the encrypted web traffic over the internet. The standard port for HTTPS is 443. HTTPS provides encryption by using an SSL certificate. Similarly, other secure practices such as DNS over HTTPS, secure SMTP, blocking SMB ports 139 and 445 at the perimeter would add to reducing your attack surface.
HTTP is the prior version of HTTPS that serves the purpose of loading web pages using hypertext links. It governs the client and server on how to communicate over the internet. HTTP does not provide any protection to the data while transmitting and does not support any encryption.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.