Almost everybody in this world uses the Internet. Some use it for work, some for education, some to stay connected with the world and their loved ones, some for shopping, and some use it to browse the world wide web in their leisure time. DNS Hijacking or DNS redirection attacks are a widespread security threat many DNS servers face in today’s modern digital world. But before explaining the DNS Hijacking attack and getting into its complexity, it is essential first to explore the world of Domain Names Systems (DNS).
In any case, if a person is using the Internet, they are requesting the world wide web to get their queries resolved. The world wide web (WWW) serves content to the users in websites or applications, and requesting content from these websites involves a certain number of steps. The Domain Name System (or DNS) is one component responsible for ensuring that the user is served the requested content. For example, if the user wishes to search the Internet using google.com, DNS’s responsibility is to ensure that the search query is carried out via google.com and that the user stays on google.com. But as with every technology, DNS also has security vulnerabilities resulting in DNS hijack.
Some of the findings shared here are from our assessments when we performed Active Directory Security Assessments or delivered various forms of network pen tests. In this article, we’ll first take a refresher of how the DNS works; then we’ll move forward with discussing DNS Hijacking – what it is, its types, its security implications and mitigation techniques.
What is DNS?
The domain name system (DNS) is a database of domain names for digital assets translated to particular Internet Protocol (IP) addresses. The Domain Name System was created because human memory tends to retain keywords like domain names (e.g. example.com) more than a number like an IP address (e.g. 123.312.233.123).
To find a real-world association, it can be said that the Domain Name System (DNS) is like a phonebook. While we can store phone numbers of our friends and relatives without names, it may be hard to remember later on which phone number belongs to which friend or relative.
To enhance DNS security, some DNS registrars use client locks. The lock disables the option to change DNS records unless the request is made from a particular IP address. Similarly, it is impossible to remember every digital asset’s IP address, while remembering domain names is much easier for the user.
Let’s take an example scenario, Man in the middle DNS Hijack, the attacker intervenes in the communication between the user and the DNS server and serves fake IP addresses that will redirect the user to malicious websites or a user on his home laptop opens a browser and sends a request to google.com. The browser returns the google search page to the user. But behind the scenes, the DNS servers translate the google.com domain name into the IP address of the server hosting Google search engine.
While there may be many stages involved in this process, the picture to the end-user stays as straightforward as hitting a request to any domain and getting the relevant response from the browser.
Since so many websites live on the Internet today and more are created every day, the DNS Mapping process is distributed among many categories of DNS Servers.
For example, an organization running internal applications which are not exposed to the Internet have no need of defining their DNS records on public DNS servers. Instead, the organization can host a local DNS server and utilize it to resolve DNS queries for internal assets.
How does DNS work?
Domain Name System (DNS) resolution process involves translating a domain name into its corresponding IP address. Like every human who wants to stay connected with other humans needs an address or a phone number, every computer or server which is part of the Internet has an IP address.
However, since the IP address is a machine-friendly address, the DNS resolution process which converts this machine-friendly address to a human-friendly address is of paramount importance.
The process of DNS resolution involves converting a hostname (such as www.example.com) into a computer-friendly IP address (such as 192.168.1.1). An IP address is given to each device on the Internet, and that address is necessary to find the appropriate Internet device – like a street address is used to find a particular home.
When a user wants to load a webpage, a translation must occur between what a user types into their web browser (example.com) and the machine-friendly address necessary to locate the example.com webpage.
Types of DNS Servers involved in loading a website:
There are 4 DNS servers involved in loading a webpage:
DNS recursor
The recursor can be thought of as a librarian who is asked to find a particular book somewhere in a library. The DNS recursor is a server designed to receive queries from client machines through applications such as web browsers. Typically the recursor is then responsible for making additional requests in order to satisfy the client’s DNS query.
When a user requests a website on his browser, the DNS resolution request is first sent to the DNS Recursor (also known as a recursive resolver). Depending on the cache status, the DNS Recursor will either respond with cached data or forward that DNS requests to other DNS servers subsequently. These requests include:
- First request to Root Name Server
- A second request to a TLD (Top-Level Domain) nameserver.
- Third and last request to an authoritative nameserver.
The reply from the authoritative nameserver contains the resulting IP address against the requested domain name and it is forwarded by the DNS recursor to the client. The response from the authoritative nameserver is also cached locally by the DNS precursor.
This process is performed so that if a subsequent request to the same website is received, the DNS recursor does not have to go through all the stages, and it can just respond to the client with the IP address value from its cache.
These DNS recursors are generally provided to the internet users by their Internet Service Providers (ISPs).
Root name server
The root server is the first step in translating (resolving) human-readable hostnames into IP addresses. It can be thought of like an index in a library that points to different racks of books – typically, it serves as a reference to other more specific locations.
As explained at the beginning of this article, DNS resolution is a hierarchical process; the root zone is the peak of that hierarchy. Root DNS servers can respond to a query from DNS recursor from its cached database of domain names or forward the query to the appropriate Top-Level Domain (TLD) Server.
The TLD Server enumerates the authoritative nameservers until it finds the correct one i.e. the DNS record that contains the requested IP address.
Root servers have an integral role in the world of the Internet, websites and browsers. The requests sent to root servers are handled by 13 different IP addresses. These 13 root servers serve the root zone. However, multiple redundant servers exist to ensure the availability of DNS requests to the root zone.
TLD Server
The top-level domain server (TLD) can be thought of as a specific rack of books in a library. This nameserver is the next step in the search for a specific IP address, and it hosts the last portion of a hostname (In example.com, the TLD server is “com”).
The top-level domain server (TLD) stores information of domain names categorized by domain extensions (e.g., .com., org.). If a user opens up the browser and enters google.com in the URL address bar, then after receiving a response from TLD Server, the DNS recursor would send the request to .com TLD Server, which would, in turn, result in the appropriate Authoritative nameserver.
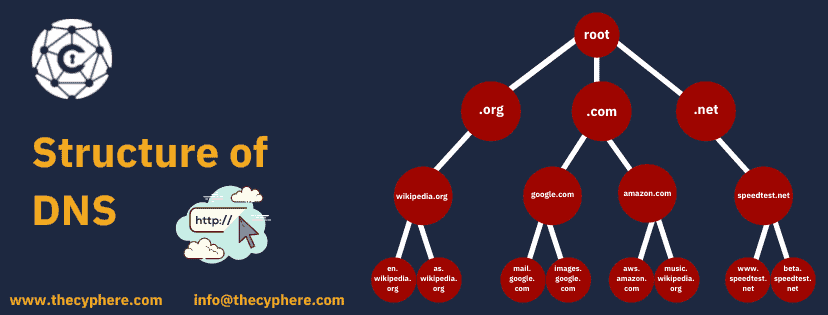
Internet Assigned Numbers Authority (IANA) is the sole manager of TLD nameservers. The TLDs are categorized into two main categories:
1. Generic Top-Level Domains: These domains are specific to the type of organization. Some common examples are (.com, .org, etc.)
2. Country Code Top-Level Domains: These domains are specific to the country or state. Some common examples are (.uk, .us, etc.)
Authoritative Servers:
Once the response is received from the TLD name server to the DNS recursor, the next and final step for the DNS recursor is to contact an authoritative nameserver. Unlike the previously discussed nameservers, the authoritative name servers contain exact IP address information (i.e. the A record for google.com etc.)
Example Scenario:
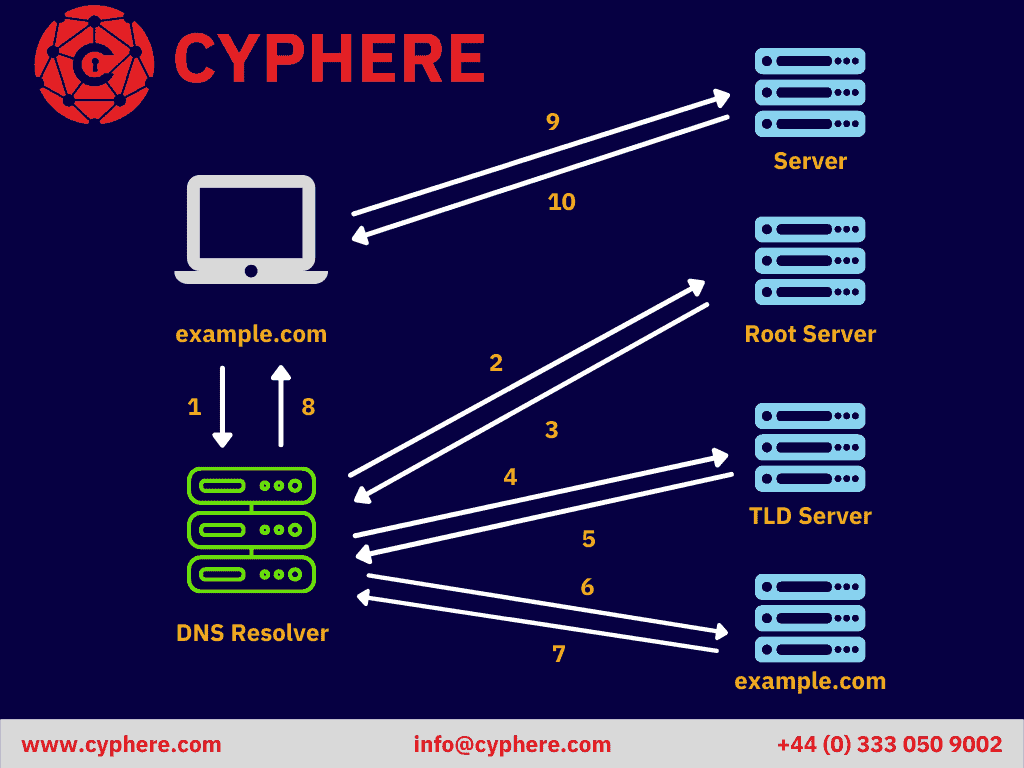
To sum up the explanation of above-mentioned DNS servers, it can be said that the following steps are an integral part of a DNS lookup:
- A user requests a ‘google.com’ page on a web browser. The query is routed via the Internet to the DNS recursive resolver.
- The resolver takes the query to a DNS root name server.
- If the address exists in the root server cache, the root server responds with the A record. If not, the root server requests for a TLD server and responds with the relevant TLD (.com, net. etc.)
- The resolver then contacts a .com TLD.
- The .com TLD responds with the IP address of the authoritative server that contains the A record for the requested domain.
- Lastly, the DNS recursive resolver requests the authoritative server for the DNS record.
- The authoritative nameserver responds with the A record of google.com that contains the IP address against the requested domain.
- The DNS recursive resolver then forwards the received response from the authoritative name server to the client browser so that the browser may request the IP address of the webserver for the web page.
What is DNS hijacking?
DNS hijacking, also known as DNS Redirection or DNS Poisoning, is an attack in which the DNS queries are wrongly resolved in order to redirect the users to a malicious website. There are many ways for the attacker to perform DNS hijacking. However, the attacker’s goal is always the same, i.e. redirect the victim to the attacker-controlled web server while the victim believes that they are on the legitimate website.
The impact of DNS hijacking can be severe for an individual or organization if the attack is orchestrated perfectly. Using the combination of website cloning, social engineering and DNS hijacking, the attacker can even steal user credentials of his social networks and banking applications.
An analogy of the DNS hijacking attack can be established with a rail and a railroad. The diversions on a train track are remotely controlled. Rogue DNS Server attackers can hack a DNS server and change DNS records to redirect DNS requests to malicious sites.

Imagine a train going towards its destination, and someone suddenly changed its course by toggling with the switch; the train will move away from its original destination and will end up at some other place, i.e. the train will be hijacked.
DNS hijacking attack works in the same way, an attacker controls the DNS traffic and sends legitimate users to malicious sites.
How does DNS hijacking work?
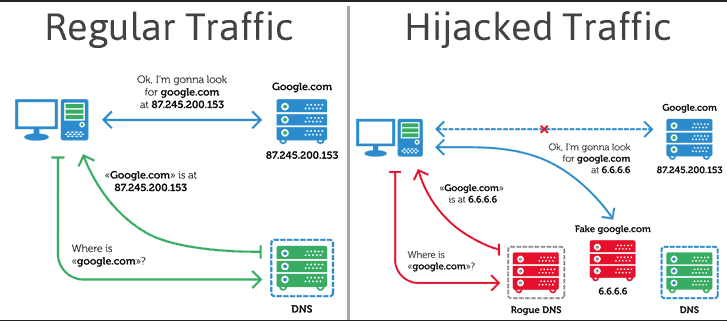
DNS settings are usually provided by the Internet Service Provider (or ISP, in short). Or in some cases, public DNS servers are used, like the one provided by Google.
FAQ: What does changing your DNS to 8.8 8.8 do?
A: 8.8.8.8 is a public and free DNS server provided by Google. Changing your DNS settings to 8.8.8.8 allows you to use the free Google DNS server.
When a website is requested, your computer makes a DNS request to the DNS server, and from there, you are redirected to the website of your choice.
If your computer DNS settings are compromised, this request is made to a rogue DNS server, and the malicious DNS server translates your DNS requests into a fake and malicious IP address and then redirects you to that fake website.
What can an attacker achieve by a DNS hijacking attack?
Same as with phishing and social engineering, DNS hijacking attack may force the users to install malware, which might give the threat actor a permanent backdoor into your system, or ransomware which may encrypt your entire file system until you pay the ransom, or spyware to keep track of your activities, so on and so forth.
DNS hijacking attack may also redirect users to a seemingly legitimate website which may force the victims to give out their sensitive and personally identifiable information (PII).
What are the types of DNS hijacking attacks?
There are four basic types of DNS hijacking attacks:
1. Local DNS hijacking
Local DNS Hijack is a type of DNS hijacking which is unique in the way that they do not necessarily originate from any network attacks like network sniffing etc. Instead, a local DNS hijack occurs when a malicious attacker compromises a computer on the Internet and now controls the system with administrative rights. By exploiting this gained access, the attacker installs a DNS-changer trojan which modifies the local DNS settings of the victim system and redirects the victim to his own malicious web server.
2. Router DNS hijacking
Many routers have vulnerabilities in their firmware or people and organizations use default usernames and passwords for their routers. Attackers may take advantage of firmware vulnerabilities or brute-force for weak or default router credentials to take over the target router DNS and change the DNS settings in the router DNS, which will consequently affect all the users connected to that router, resulting in router DNS hijacking.
3. Man-in-the-Middle (MITM) DNS hijacking attack
MITM is the type of DNS hijacking in which attackers may intercept traffic and network communication between a user and the DNS server and attempt to change the destination IP address and redirect the innocent user to a malicious site.
4. Rogue DNS server
In this attack, the attackers directly exploit any weakness or vulnerability in the DNS server itself. Attacker gains system-level access to the DNS server by either exploiting any known vulnerable application, weak credentials, insecure network services etc.
The system-level access of the DNS server allows the attacker to conduct the attack on a vast scale since the attacker controls the DNS resolution for multiple clients instead of manipulating the DNS resolution of individual clients.
These attacks may also be very subtle and hard to detect if the attacker can create similar looking websites to ensure the users are not alerted to any suspicious activity in their daily browsing routine.
What are the methods to protect against DNS hijacking attacks?
The mitigation techniques for DNS hijacking can be divided into three parts:
1. Mitigating nameserver hijacking
Attackers may take over DNS servers and modify them to rogue DNS servers if they are misconfigured or have security vulnerabilities. Therefore, the first and foremost thought should be to secure the DNS servers.
i. Endpoints and Servers Hardening:
Any organizations that run their local DNS servers should ensure that their endpoints and DNS servers are hardened. By hardening, it is implied that:
- No known vulnerable applications or services are running on the servers.
- No unnecessary port connections are allowed.
- Security release notes are monitored regularly for any potential security updates.
ii. Install firewalls and monitor logs:
Firewalls allow an organization to prevent traffic from and to unwanted IP addresses. In case of a DNS hijacking attack, firewall logs can reveal DNS requests being made to bad reputed IP addresses. These logs should be monitored to detect any spoofed DNS configurations.
iii. Prevent web-cache poisoning
Randomize user identities, server source ports and use both upper and lower case letters in your domain names.
iv. Prevent zone-transfers
Make sure that DNS servers don’t have zone transfer vulnerabilities, as zone transfers allow attackers to get all the information from the DNS server.
2. Mitigation measures for end-users
i. Prevent use of default credentials
End-users can prevent DNS hijacking by changing their default router credentials. End-users should also regularly monitor their /etc/hosts/ file in order to ensure that no unauthorized DNS entries are made by DNS-changer trojans.
ii. Regular updating and constant patching
Keeping their systems up to date, installed with the latest application and operating system patches, and using an endpoint security solution.
iii. Encrypted VPN
Using an encrypted VPN channel.
iv. Public DNS service
Using public and more secure DNS services like Google’s Public DNS, Google’s DNS over HTTPS (port 443) and Cisco OpenDNS
3. Mitigation measures for website owners
i. Use secure access
Keeping in mind the Principle of Least Privileges, allow DNS access to only a few members of the IT team and also enforce the use of multi-factor authentication upon accessing DNS servers.
ii. Use client lock
Client lock, also called change lock, prevents the modification of DNS records unless from a specific and allowed individual and/or IP address.
iii. Use DNSSec
DNSSec digitally signs DNS communication, making it a bit difficult for attackers to intercept and modify DNS traffic.
How to check if your DNS has been hijacked
To check whether or not your DNS is hijacked, regularly check the contents of your host’s file. The presence of any unusual or unrecognized entries in the host’s file may indicate that your DNS settings have been hijacked.
In Windows, the host’s file is located at the following location:
C:WindowsSystem32driversetchosts
To view the contents of the file, either open the file in a text editor of your choice, or use ‘type’ or ‘more’ to view the contents of the host file from the command prompt, or ‘cat’ to view it with Powershell.
In Linux based systems and macOS, the host’s file is present at the following location:
/etc/hosts
You can view the contents using ‘cat’ from the terminal, or opening the file in the text editor of your choice.
What is the difference between DNS hijacking or DNS redirection and DNS spoofing?
DNS spoofing and DNS poisoning (or DNS cache poisoning) are the same things, but slightly different from DNS hijacking. In the latter, an attacker would either plant malware or compromise the router’s DNS settings. However, in DNS cache poisoning or spoofing, the attackers compromise (or poison) the cache of a DNS server.
DNS redirection, on the other hand, is an unethical way of redirecting users to unintended pages such as advertisements pages, etc. ISPs are the ones that usually practice DNS redirects to drive users, say from a 404 page to their desired pages which are usually ad pages, therefore DNS hijacking may also be named as ISP DNS hijacking.
Some real-world cases of DNS hijacking attacks
Here are some of the real-life examples where large impacts were noticed due to DNS configuration going wrong (due to security incidents or configuration problems).
1. Twitter, New York Times & Huffington Post DNS hijack
In 2013, DNS servers of Twitter, the New York Times and the Huffington Post were hijacked as they were owned by the same organization, an Australian internet company.
2. The Sea Turtle DNS hijacking attack
The Sea Turtle campaign, which apparently was a nation-state backed DNS hijacking campaign, spread across 13 countries and targeted at least 40 public and private entities. The threat actors behind Sea Turtle used changed DNS records to reroute victims to spoofed sites where they then stole login credentials.
3. WikiLeaks name servers DNS hijacking
In 2017, WikiLeaks users were redirected to a fake website. Instead of seeing a number of controversial articles and documents, the users were shown an unusual message.
The threat actors, the notorious OurMine group, didn’t compromise the WikiLeaks server to redirect the users to their website but hijacked the name server, as explained by WikiLeaks founder, Julian Assange, in his tweet:
“WikiLeaks servers have not been hacked. There have been two types of internet infrastructure (DNS) attacks. Always use HTTPS or our .onion.”
4. The ICANN DNS hijack attack
The Internet Corporation for Assigned Names and Numbers (ICANN) is a renowned name on the Internet. It is responsible for maintaining the security of namespace databases. Similarly, in 2008, the ICANN.com domain name was hijacked by a Turkish group of threat actors, NetDevilz.
Conclusion
DNS is the backbone of the Internet, where our digital lives breathe. Without this, our real lives (think of pharmacies, doctors issuing prescriptions, ordering groceries, or any other routine tasks of daily life) will almost certainly be impacted.
How good is your organization’s cyber hygiene? An IT security health includes reviews around business-critical assets composed of Active Directory and related components such as DNS, DHCP that keep an organization’s internal and external networks alive.
Get in touch to schedule a consultation call or schedule a pen test today.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.