
Our article provides an overview of the most common forms of computer viruses along with some punches of computer fun facts, history & interesting facts about computer viruses and other types of malware. A few weeks ago, we also published cyber security glossary, simplifying geeky terms for general readers.
Whether you use a tablet, a mobile phone, a laptop or another device with internet connectivity, your device has an attack surface on the internet. Attackers are stepping up their learning game to target new and old technology users with varied techniques. The very first step to protecting yourself online is understanding what you are up against. On a lighter note, fake virus pranks used to be popular in the last decade to freak out friends.
The most common term we come across today is malware. It is a malicious computer program installed without the consent of users that performs unauthorised actions such as data access, data theft or controlling the victim computer. Here is an overview of different types of malware, computer worms facts and the threats posed by these variants. Although there is an exhaustive list of computer viruses identified to date, our article is all about high-level computer virus facts and information as a light read. This is not meant as a deep-dive or a post of technical nature. If you are looking for information on computer viruses, their types and what they do, you are in the right place.
What is a computer virus?
Viruses are a type of malware that earned their name because of how they spread around. This piece of software infects other files on disk drives or machines when downloaded as a program from websites, data transfers via removable media, shared drives or email attachments.
What was the first-ever computer virus?
Creeper was the first computer virus created in 1971 – a worm that was self-replicating – written by Bob Thomas of BBN that targeted computers connected to ARPANET (designed by ARPA, a division of US Dept of Defense). It was not written to cause any harm and displayed a message that read ‘I’M THE CREEPER. CATCH ME IF YOU CAN!’.
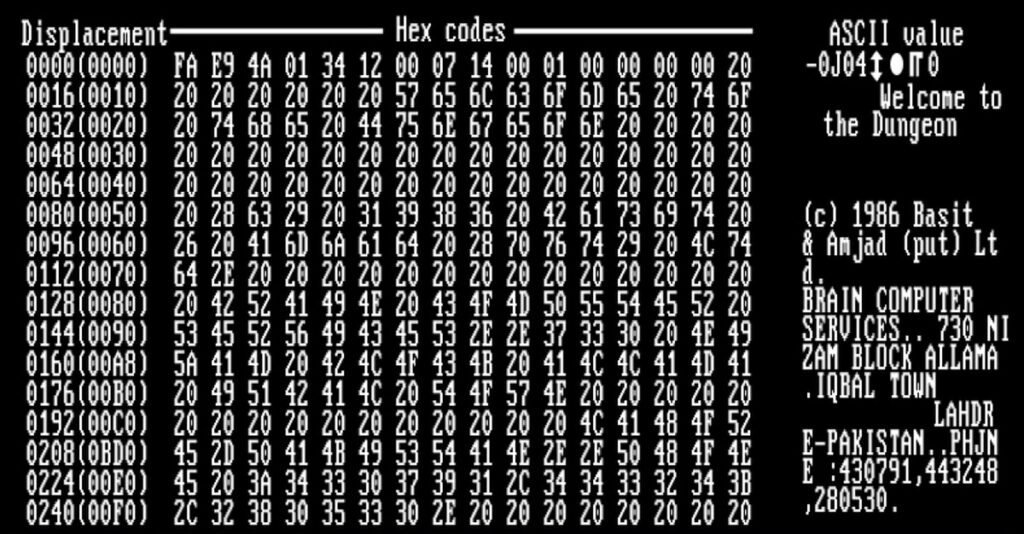
Brain Virus
‘Brain’ was the first computer virus for MS-DOS (non-graphical command line operating system from Microsoft) that appeared around January 1986 that was created by two Pakistani brothers. They were tired of customers pirating software from their shop and then ‘brain’ was designed to infect the boot sector of floppy disks.
Fun fact about floppy disk
Floppy disks were 5.25 inch disks dubbed ‘floppy’ because diskette packaging was made out of flexible plastic. More rigid floppies started in 3.5 inch sizes. Last time I checked there were a few available on e-bay (might be a souvenir for geeky friends!)
As further pirated copies were made, the virus spread from disk to computer drives, loading onto the new machines.
Screenshot from Mikko Hypponen’s trip to Lahore, Pakistan to meet the authors of Brain virus.
Melissa Virus
Melissa virus was released around March 1999 that was a mass-mailing macro virus (not a standalone program) that targeted Microsoft Word and Outlook applications. The exploitation of the same macros is very much part of today’s red teaming and technical security assessments. Such ethical hacking simulation exercises (against web applications, mobile, networks, systems) are performed against businesses to help them improve security controls against real-world cyber attacks.
The carrier of this virus was an email titled ‘Important Message From ’. You see that social engineering techniques and email mediums used to spread malicious content started with this incident. This led to thousands of computers being infected, causing billions of dollars in losses across multiple countries.
BTW, who was Melissa? This virus was created in the memory of a stripper in Florida.

Worms
Worms are standalone computer programs that replicate themselves. Unlike viruses, they don’t need human interaction and propagate across networks via internet, email, instant messaging worms, file-sharing and IRC (Internet Relay Chat) channels. A few popular examples of computer worms are provided below.
The Morris Worm
Around 30 years ago, Robert Tappan Morris, a student of Cornell University, launched this worm in 1988 in quest of finding out how big internet was. However, to his surprise, the bugs in the code led to thousands of computers. A few interesting facts about Morris Worm are:
- It infected about 10% of the computers (total 60,000 computers) on the internet (the only malware case in history to reach this magnitude).
- It did not destroy any files however vital military and university functions struggled to continue.
- The exact financial damages remain unknown, though estimated to be in millions.
- Robert Tappan Morris was prosecuted under the fraud and deception charge, the first-ever case under the Computer Fraud and Abuse Act,1986.
This incident had a huge impact on society in terms of how important computers had become, giving birth to the seriousness of cybersecurity.
Trojan Horses
Often called ‘trojans’, based on the story of the wooden horse used to trick Troy defenders, are a type of viruses that masquerade as computer software or legit files. When downloaded on a victim’s computer, trojans execute to perform certain tasks such as stealing information or other malicious activities without the user’s consent.
Most commons forms of trojan horses include:
- RAT stands for Remote Access Trojan and is one of the most popular trojans that is designed to allow remote access control to an attacker.
- Backdoor trojans allow access to their handlers (attackers) to keep a communication channel open for transferring of data, system control or allow for further exploitation.
- Downloader trojans work to download additional content onto the infected computer, such as additional malicious content to perform specific tasks or spread on the network.
SQL Slammer
In 2003, this computer worm caused Denial of Service (DoS) on systems connected to the internet, slowing general internet traffic by spreading rapidly and infecting around 75,000 victims within 10 minutes. This worm exploited a bug in the Microsoft SQL Server 2000 and Microsoft Desktop Engine (MSDE) 2000 (database products) that already had a patch available. However, many organisations had not applied this patch that was released six months prior to this incident (MS02-039).
This worm was based on a proof concept presented at Black Hat by David Litchfield, the known
Adware
This is one of the most common nuisances, automatically delivering popup ads on web pages and advertising messages. These are delivered as part of the free software downloaded by users. Adware wasn’t originally meant to cause harm to computers but used to collect information from users’ browsing history and files. These programs are technically installed with the user’s authorisation, more often through the small print when multiple pages of Terms of Use are displayed on your screen where the only way to get through is granting consent or clicking ‘I agree’ buttons.
If you ever observed your search engine preferences or website redirects happening automatically, that is an adware program in action.
Top 6 Most Ridiculous Virus Myths
The following infographic explains the most common computer virus myths. It is important to be aware of virus myths that may jeopardise your data security.

Spyware
Just what it says on the tin! A piece of code (software) that enables a user to obtain covert information about the target computer. It is designed to operate in stealth mode and is often used for malicious purposes. Most common examples are programs installed on your computer without your consent meant to steal your sensitive information such as passwords, PIN, and payment information and transmit it back to their controllers (attacker computers). Spyware programs are distributed as ‘shareware’ or ‘freeware’ to avoid licensing restrictions to cast its’ net as wide as possible.
Legit examples of spyware include employers utilising programs at a workplace or parental control programs. However, in today’s workspace, it is almost assumed that all such programs are notified to employees via their employment contract or security policies defined within the organisation.
Ransomware
Ransomware is a targeted approach that aims to take control of a victim’s computer or networks to lock files to demand a ransom. These files are locked (encrypted) in a way that only the party that has unlocking key (decryption) can get back data in clear-text form (readable format). To get back files and gain access to a system, attackers demand ransom payments in return for the decryption key. Therefore, this makes an interesting fact on viruses for attackers to use it for their wins.
Ransomware victims usually access these through ransom emails that contain links. These emails pretend to offer a free item or change a password to an old account. Many emails have become more advanced to look indistinguishable from legitimate ones, which means checking the email address of the sender is a must. When a person’s email address is hacked, the hackers will likely use it to send more ransom links to other addresses in a person’s contact list.
This is often a well-planned operation normally part of the organised crime groups targeting small and big companies. This includes government organisations such as local councils, and bigger corporations such as Garmin, Norsk Hydro. Many companies have paid the ransom to get back their files, however, this is not something guaranteed to work.
Should you pay the ransom? There are two sides to this question, just like any other question. The decision to pay ransomware demand should not be taken lightly. It comes with the acceptance of several risks and in coordination with legal counsel, cyber insurance and security experts. Should decide to pay ransomware, you need to be aware of a number of factors. To know what should an organisation do if they get hacked, read our detailed article on malware and ransomware protection.
Bots
Bots are automated programs designed to perform specific tasks, such as finding websites running a specific version of the software that is prone to bugs, executing specific commands without the user’s approval or infecting computers over the internet to create a vast network of attacker-controlled computers. Bad bots are often used by attackers to create a network, just like a gang of computers often used to target victims in Distributed Denial of Service attacks, or perform specific campaigns such as stealing sensitive data, ransomware or spam campaigns.
About Cyphere
We help businesses protect their most prized assets by securing their cybersphere. This includes carrying out independent technical security assessments to identify gaps and provide an accurate risk posture to help customers handle their digital risks. Get in touch to discuss your primary security concerns, it includes a free consultation call to advise you without any salesy-pushy tactics.
Harman Singh is a security professional with over 15 years of consulting experience in both public and private sectors.
As the Managing Consultant at Cyphere, he provides cyber security services to retailers, fintech companies, SaaS providers, housing and social care, construction and more. Harman specialises in technical risk assessments, penetration testing and security strategy.
He regularly speaks at industry events, has been a trainer at prestigious conferences such as Black Hat and shares his expertise on topics such as ‘less is more’ when it comes to cybersecurity. He is a strong advocate for ensuring cyber security as an enabler for business growth.
In addition to his consultancy work, Harman is an active blogger and author who has written articles for Infosecurity Magazine, VentureBeat and other websites.












